Content
Inspect Your Ports – test udp port
Open Port Check Tool:
A slot is actually a variety that works with an entrance to a service that levels to the system.
In pc systems, an available port is a port that presently utilizes (open) by a company. An available slot can be actually utilized to send or/and receive records over the system.
- To scan individually, pick 'specific', input a valid port number, and select 'Check'.
- You can also use the Next-door neighbor Map as well as Route Viewer devices in ETS for a noticeable summary of how your network is transmitting.
- With the SNMP MIB web browser, you can query SNMP-managed devices to check out setups and various other MIB qualities.
- Network ports are the communication endpoints for a machine that is attached to the Web.
- Ports vary in their methods as well as the types of solutions they provide.
TCP slots as well as UDP ports. Open up port check resource can easily inspect the state of a TCP slot.
An example can be your internet internet browser on the client-side and an internet hosting server as the remote control web server.
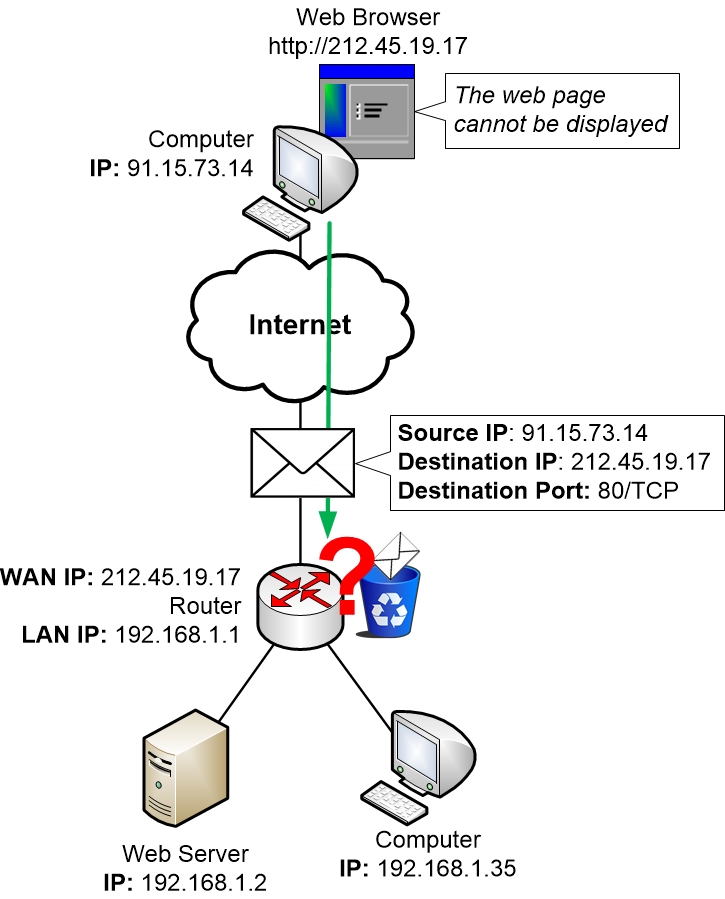
The internet hosting server uses the nonpayment port 80 for HTTP or port 443 for HTTPS to listen closely as well as wait for hookups. Your browser develops a relationship to that port, using a nearby port. Once it linked they send and also obtain data in between them. An available port inspection device can be actually used to check out if the port is presently open or even not on an intended device.
It feels like a port test, utilizing this tool you can easily also recognize port sending status.
If your hosting server is being actually blocked through a firewall, you can easily also utilize an available port inspection tool to from another location check.
Slot Scanner: A slot scanning device is a resource that could be used to check a variety of ports.
An additional sophisticated or even port checker can easily browse some deal with or also a full system seeking ports that level. In pc security as well as hacking it is actually commonly made use of to hunt for challenging open ports that intend to be near or even monitor. An available port is like an available door or a window. Along with the best expertise, it is feasible to utilize this port to take part in the remote pc.
Utilizing and also running a routine slot check is an excellent approach to discover available ports and finalize them. , if an available slot is discovered it is actually additionally made use of to know why as well as that open it.
.
What Is A Port Scanner? – port checker
There are some extremely valuable resources that may be made use of to check the network deal with for available ports. Utilizing such resources can even find address inside the institution that needs to be actually removed.
An instance of system slots scanner device is actually Nmap. Using it you can easily browse total subnet. It supports a number of scan techniques like here TCP SYN check and also TCP ACK browse. Advanced usage of the device can easily locate what is the solution (method) that open up the operating and also the slot unit backing this solution.
Online port scanner:
The aged craft of slot scanning is still functioning. Also thou that today there is a much more safe procedure to shut and monitor slots as well as companies in the operating atmosphere.
. An Intrusion diagnosis unit (IDS) may be used to keep an eye on the network.
Along with the accelerated of new devices, an online port scanning device device could be used as a resource to scan a setting. Checking from outside the organization.
An on the web port scanner is a port scanner like any kind of various other slot scanning device. The only deferent is actually that it operates coming from outside your network. re: a website-- online.
If you have excessive open ports on your computer/device that requires to be closed, it is actually a great tool that can be used to inspect.
Solutions that count on the Web (like web browsers, websites, as well as data transactions solutions) rely upon certain slots to broadcast as well as receive information. Creators utilize file transmission protocols (FTPs) or SSH to operate encrypted tunnels around computers to discuss information between hosts.
Once a service is operating on a certain slot, you can not run various other companies on it. For example, starting Apache after you've already started Nginx on port 80 will lead to a neglected function given that the slot is actually actually in operation.

Open ports become dangerous when legitimate companies are actually manipulated via safety susceptibilities or destructive solutions are presented to a system via malware or even social planning, cybercriminals can easily utilize these services along with available slots to get unapproved access to sensitive records.
Closing remaining ports decreases your safety danger through lowering the amount of strike angles your association is exposed to.